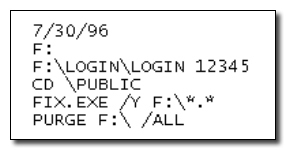
Today In Infosec on Twitter: "2006: The Forensic Files episode "Hack Attack" aired. It covered a logic bomb activated in 1996 at Omega Engineering, for which Tim Lloyd was later convicted. https://t.co/EJqXp5F9kX" /
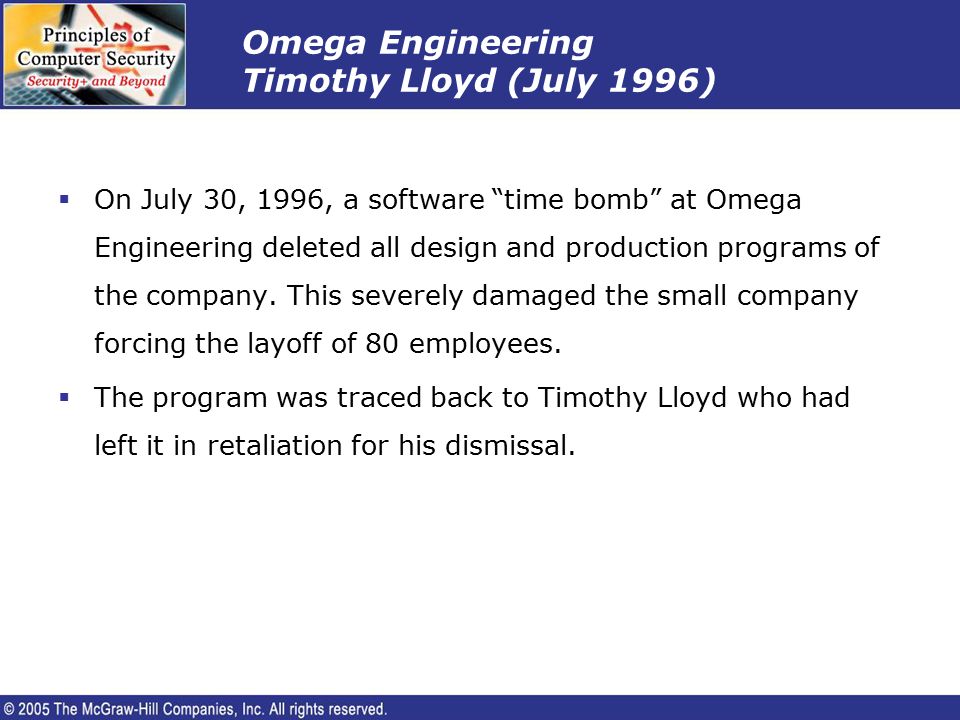
Lesson 1-Introduction and Security Trends. Background Terrorists have targeted people and physical structures. – The average citizens are more likely. - ppt download
West Virginia State University - Marquis Who's Who Selects Eric L. Jackson for Success in Higher Education Administration

IS4463 Secure Electronic Commerce 5:30-6:45 PM Robert Kaufman –Background –Contact information Syllabus and Class Schedule Student Background Information. - ppt download